1] E. Alata, M. Dacier, Y. Deswarte, M. Kaaâniche, K. Kortchinsky, V. Nicomette, V. H. Pham, and F. Pouget. Collection and ana

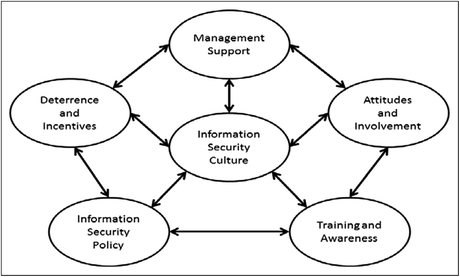
Information Security Compliance in Organizations: An Institutional Perspective in: Data and Information Management Volume 1 Issue 2 (2017)

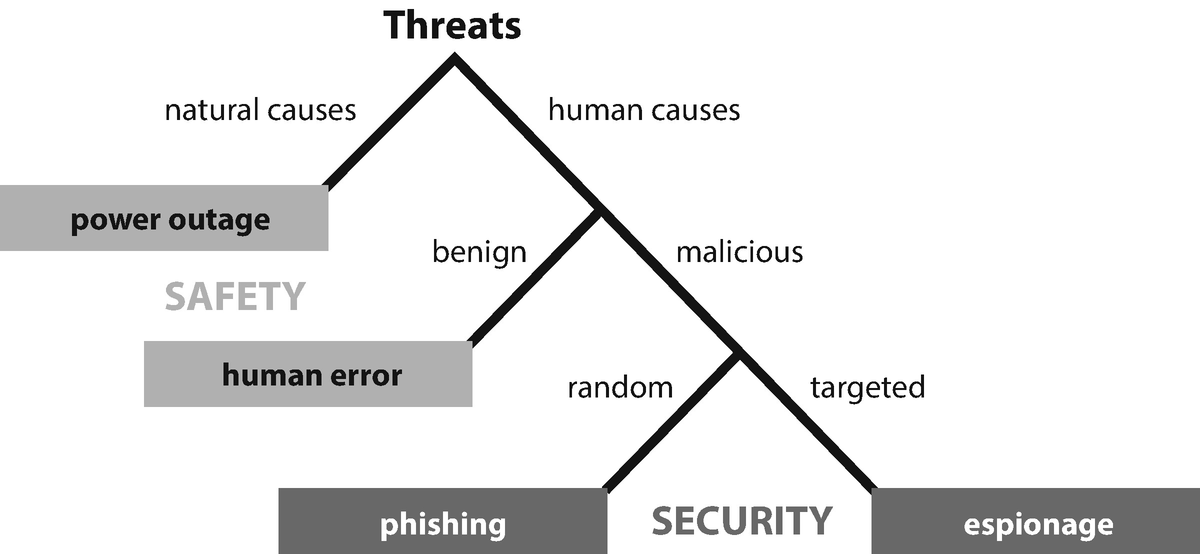
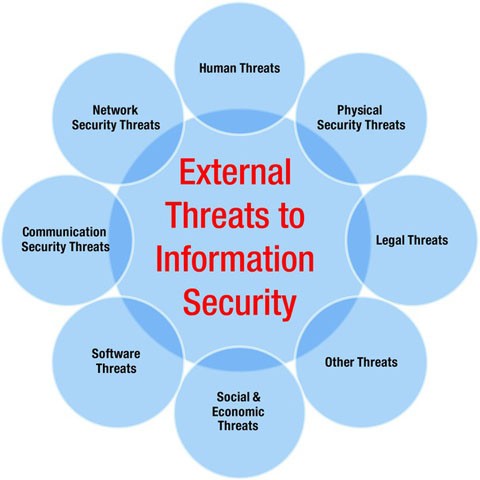
Enterprise data breach: causes, challenges, prevention, and future directions - Cheng - 2017 - WIREs Data Mining and Knowledge Discovery - Wiley Online Library

Enterprise data breach: causes, challenges, prevention, and future directions - Cheng - 2017 - WIREs Data Mining and Knowledge Discovery - Wiley Online Library

Information Security Compliance in Organizations: An Institutional Perspective in: Data and Information Management Volume 1 Issue 2 (2017)