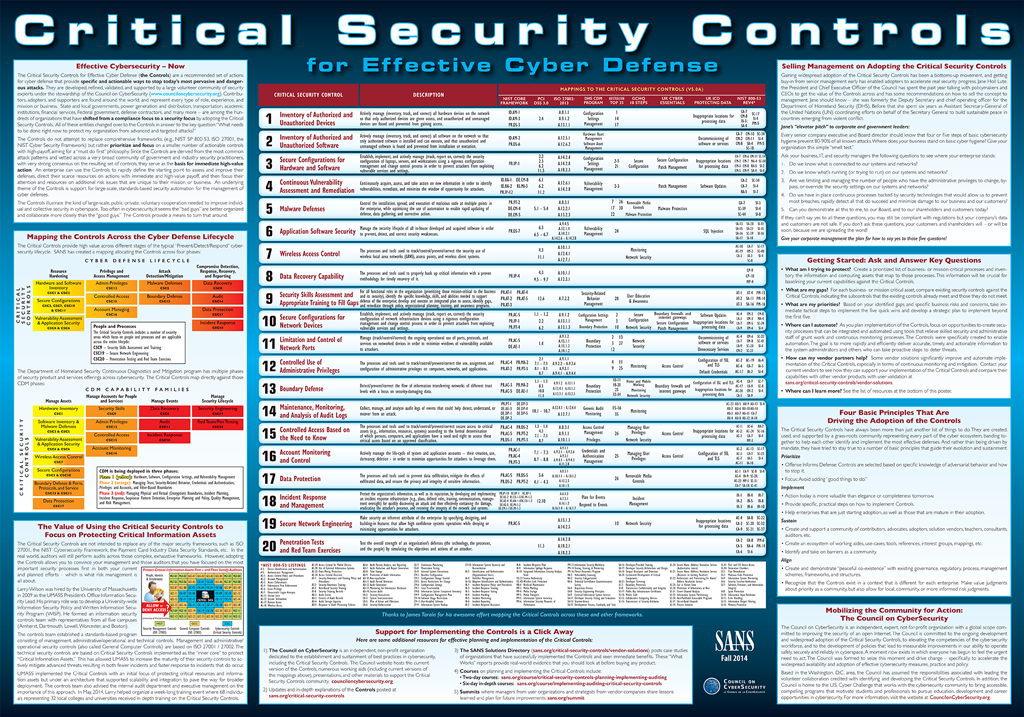
SANS Institute on Twitter: "20 CRITICAL SECURITY CONTROLS | POSTER: Set of actions for cyber defense. DL > PDF (2pgs) - http://t.co/YZGlCbuXmd http://t.co/moeIozrqu0"
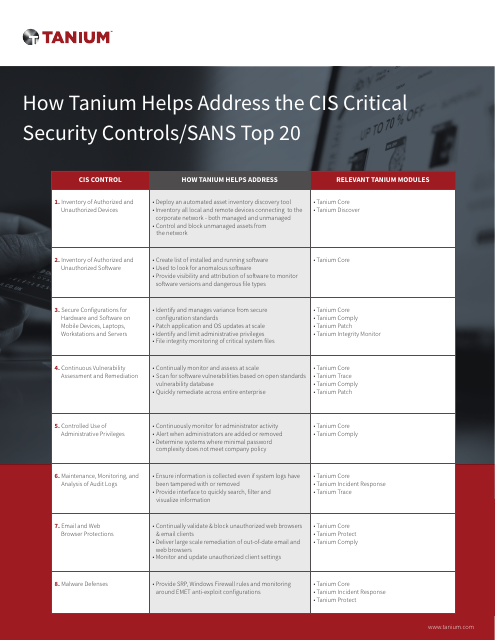
How Tanium helps address the CIS Critical Security Controls/SANS Top 20 | Cyentia Cybersecurity Research Library